In today’s digital era, mobile devices have become an integral part of our lives, serving as gateways to personal and sensitive information. With the growing dependence on mobile devices, it is crucial to implement robust security measures to protect sensitive data from unauthorized access or breaches. This article will explore various techniques and best practices for securing sensitive data on mobile devices. We will discuss data encryption, secure storage mechanisms, and secure data transfer protocols, providing practical examples and actionable tips to help readers enhance the security of their mobile devices.
Data Encryption
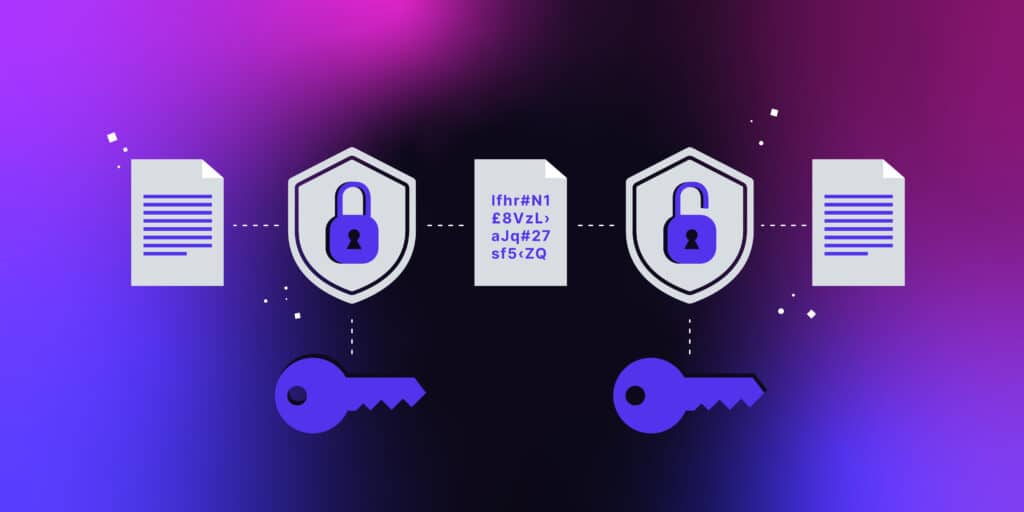
Data encryption is an essential practice for protecting sensitive information on mobile devices. By encrypting data, it becomes unreadable to unauthorized individuals, ensuring that even if the device is compromised, the data remains secure. Here are some best practices for data encryption:
- Utilize Full Disk Encryption (FDE): Full Disk Encryption is a technique that encrypts the entire storage of a mobile device, including the operating system, applications, and user data. By enabling FDE, all data stored on the device is automatically encrypted, providing a strong layer of protection against unauthorized access. FDE can be enabled through the device settings or by using third-party encryption software.
- Implement Strong Passwords or Biometric Authentication: To enhance the security of encrypted data, it is crucial to use strong passwords or biometric authentication (such as fingerprint or facial recognition) to unlock the device. Strong passwords should be complex, unique, and not easily guessable. Biometric authentication adds an extra layer of security by relying on unique physical characteristics.
- Encrypt Data at the Application Level: In addition to full disk encryption, it is important to encrypt sensitive data at the application level. Mobile app developers should employ techniques such as data encryption libraries and secure storage mechanisms to protect user data. For example, sensitive data like passwords, credit card information, or personal identification numbers (PINs) should be encrypted before being stored in the device’s memory or local storage.
Secure Storage Mechanisms
Secure storage mechanisms play a vital role in protecting sensitive data on mobile devices. These mechanisms ensure that data is stored in a secure manner and is not easily accessible to malicious actors. Here are some best practices for implementing secure storage mechanisms:
- Use Secure Key Management: To secure sensitive data, it is essential to use secure key management practices. Encryption keys should be stored separately from the encrypted data and should be protected with strong access controls. Secure key management systems, such as hardware security modules (HSMs) or secure enclaves, can provide additional protection for encryption keys.
- Secure Local Storage: Mobile devices often have local storage where apps store data. It is important to ensure that this local storage is secure. Mobile app developers should follow secure coding practices and encrypt sensitive data before storing it locally. Additionally, apps should clear sensitive data from memory when it is no longer needed to minimize the risk of unauthorized access.
- Leverage Cloud Storage Encryption: Many users store their data in the cloud for convenience. When using cloud storage services, it is crucial to enable encryption at rest. This ensures that data stored in the cloud is encrypted and protected from unauthorized access. Cloud storage providers often offer encryption options, allowing users to encrypt their data before it leaves their device.
- Implement Remote Data Wiping: In case a mobile device is lost or stolen, it is important to have the ability to remotely wipe sensitive data from the device. Remote data wiping allows users or administrators to erase all data on the device, ensuring that sensitive information does not fall into the wrong hands. Mobile device management (MDM) solutions often provide remote wiping capabilities for enterprise devices.
Secure Data Transfer Protocols
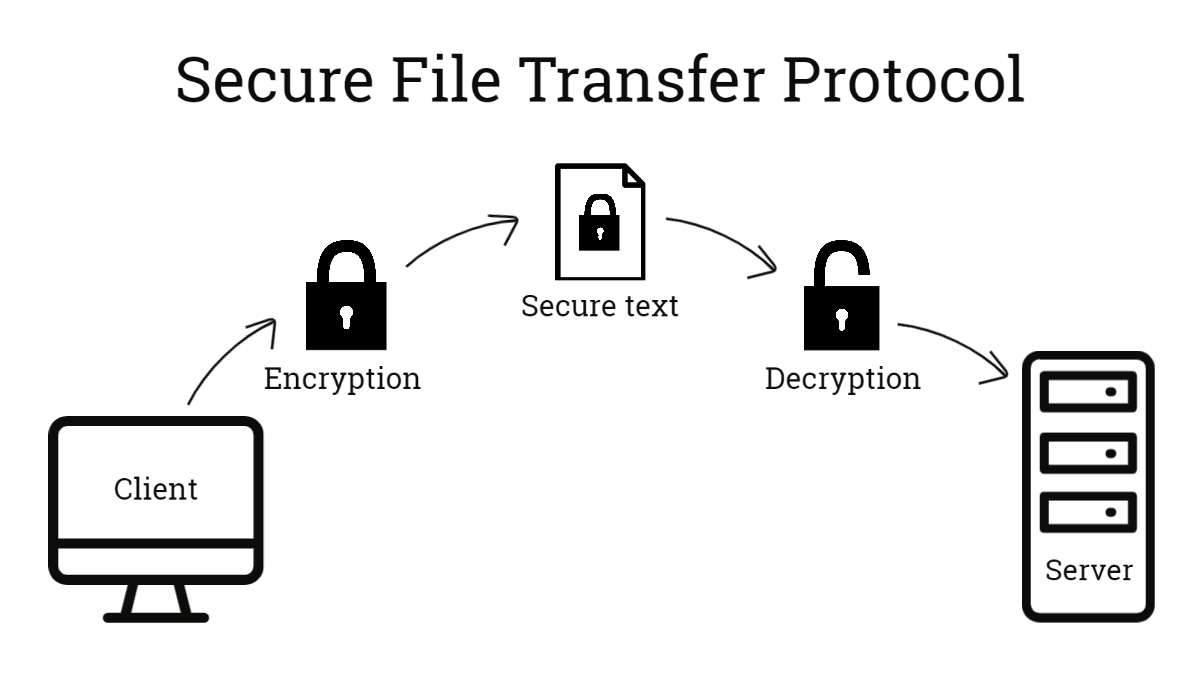
When transmitting sensitive data from a mobile device, it is crucial to use secure data transfer protocols to protect the information from interception or unauthorized access. Here are some best practices for secure data transfer:
- Use Secure Socket Layer/Transport Layer Security (SSL/TLS) for Communication: SSL/TLS protocols provide secure communication channels between mobile devices and servers. Mobile apps should use SSL/TLS to encrypt data in transit, preventing eavesdropping and tampering. It is important to use the latest versions of SSL/TLS and ensure that proper certificate validation is performed to prevent man-in-the-middle attacks.
- Implement Two-Factor Authentication (2FA): Two-Factor Authentication adds an extra layer of security during data transfer. By requiring users to provide a second form of authentication, such as a one-time password (OTP) or a hardware token, it significantly reduces the risk of unauthorized access. Mobile apps should implement 2FA for user authentication and data transfer processes.
- Secure Mobile App APIs: Mobile apps often communicate with backend servers through APIs. It is crucial to secure these APIs to protect sensitive data. API endpoints should be protected with authentication mechanisms, such as API keys or OAuth, and transmitted data should be encrypted using SSL/TLS. Additionally, mobile app developers should follow secure coding practices and implement input validation and output encoding to prevent common security vulnerabilities like SQL injection or cross-site scripting (XSS) attacks.
- Encrypt Data in Transit: In addition to using SSL/TLS for securing communication channels, it is important to encrypt sensitive data before transmitting it. Mobile apps should encrypt data using strong encryption algorithms before sending it over the network. This ensures that even if the data is intercepted, it remains encrypted and unreadable to unauthorized individuals.
Conclusion
Securing sensitive data on mobile devices is of utmost importance in today’s digital landscape. By implementing robust security measures such as data encryption, secure storage mechanisms, and secure data transfer protocols, users can significantly reduce the risk of data breaches and unauthorized access. It is crucial for mobile app developers, organizations, and individuals to prioritize mobile device security and stay updated with the latest security practices and technologies. By following the best practices discussed in this article and being proactive in implementing security measures, users can safeguard their sensitive data and maintain the privacy and integrity of their mobile devices. Remember, security is an ongoing process, and it is essential to regularly update and review security measures to adapt to evolving threats and vulnerabilities in the mobile landscape.

