Ensuring the security of sensitive data is paramount for applications that handle user information or other confidential data. Secure data storage and encryption techniques play a vital role in protecting this data from unauthorized access and maintaining its confidentiality. This article will explore different techniques and best practices for secure data storage and encryption in applications. It will cover topics such as data classification, encryption algorithms, key management, secure data transmission, secure database design, and secure file storage.
Data Classification

Data classification involves categorizing data based on its sensitivity and importance. By classifying data, organizations can apply appropriate security controls and encryption measures that align with the level of sensitivity. Here are some key points to consider for data classification:
- Identify sensitive data: Determine the types of data that require protection, such as personally identifiable information (PII), financial data, or intellectual property.
- Assign data classification levels: Classify data into different levels based on its sensitivity, such as public, internal, confidential, or highly confidential.
- Define access controls: Implement access controls that restrict data access based on classification levels. Only authorized individuals or systems should be able to access and manipulate sensitive data.
- Data lifecycle management: Establish processes for handling data throughout its lifecycle, including data creation, storage, transmission, and disposal. Apply appropriate security measures at each stage.
- Regular data classification reviews: Periodically review and update data classification to ensure it aligns with changing business requirements and regulatory compliance.
By classifying data and applying appropriate security controls, organizations can focus their encryption efforts on protecting the most sensitive information.
Encryption Algorithms
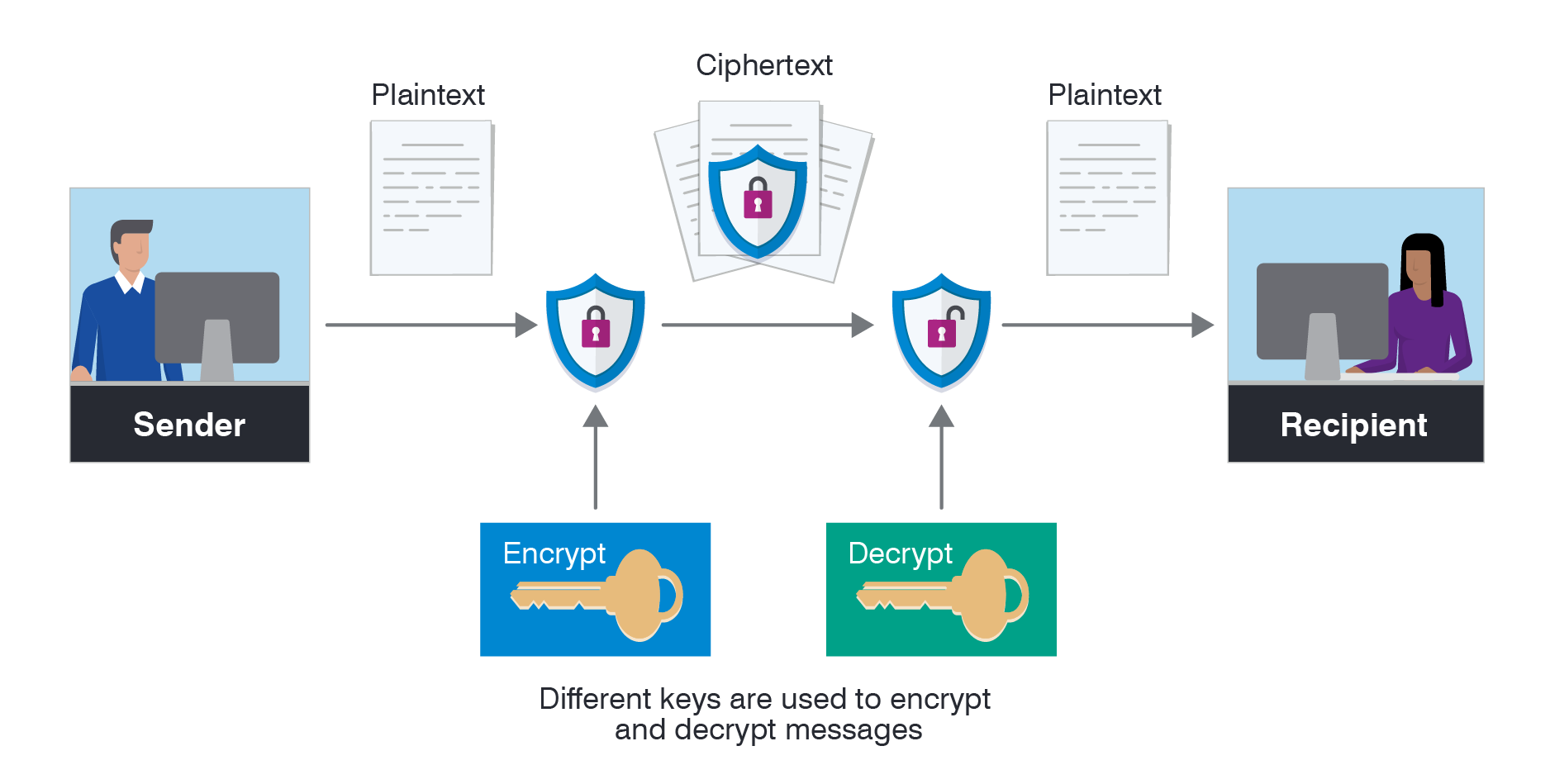
Encryption algorithms transform data into an unreadable format to prevent unauthorized access. The choice of encryption algorithm is crucial to ensure the confidentiality and integrity of the encrypted data. Here are some key points to consider when selecting encryption algorithms:
- Symmetric encryption: Symmetric encryption uses the same key for both encryption and decryption. It is efficient for encrypting large amounts of data but requires secure key management practices.
- Asymmetric encryption: Asymmetric encryption, or public-key encryption, uses a pair of keys: a public key for encryption and a private key for decryption. It enables secure communication between parties without the need to exchange a shared key.
- Hash functions: Hash functions generate a fixed-length hash value from input data. They are commonly used for data integrity checks and password storage. Strong hash functions are resistant to collisions and irreversible.
- Key size and strength: The strength of encryption depends on the key size and the security of the encryption algorithm. Longer key sizes provide more security against brute-force attacks.
- Industry-standard algorithms: Use widely accepted and vetted encryption algorithms, such as Advanced Encryption Standard (AES) for symmetric encryption and RSA or Elliptic Curve Cryptography (ECC) for asymmetric encryption.
- Regular algorithm updates: Stay up to date with the latest advancements in encryption algorithms and cryptographic standards. Deprecated or compromised algorithms should be replaced promptly.
By selecting appropriate encryption algorithms and ensuring their secure implementation, organizations can safeguard sensitive data from unauthorized access.
Key Management
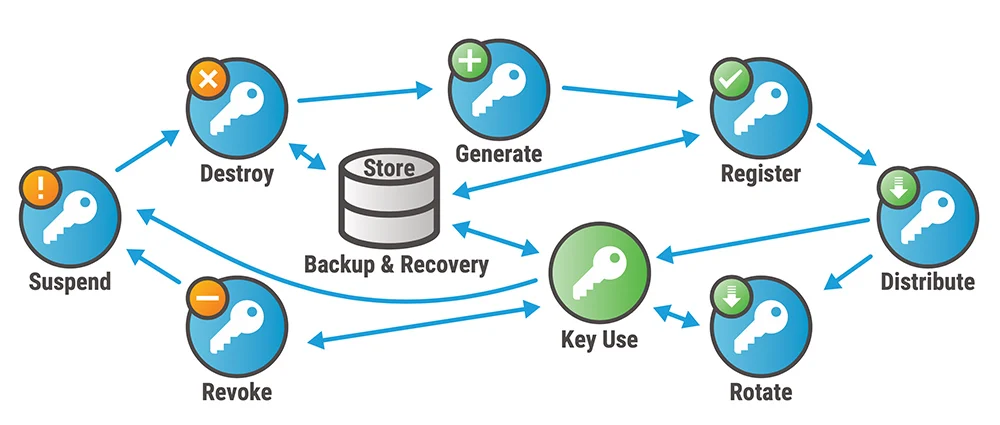
Key management is crucial for securely storing, distributing, and revoking encryption keys. Effective key management practices are essential for maintaining the confidentiality of encrypted data. Here are some key points to consider for key management:
- Secure key generation: Use cryptographically secure random number generators to generate encryption keys. Weak or predictable keys can compromise the security of the encrypted data.
- Key storage and protection: Safely store encryption keys in secure key management systems or hardware security modules (HSMs). Ensure that access to the keys is restricted to authorized individuals or systems.
- Key rotation: Regularly rotate encryption keys to minimize the impact of potential key compromise. Implement processes to generate new keys and securely replace the existing keys.
- Key distribution and sharing: Use secure channels and protocols to distribute encryption keys to authorized parties. Avoid sharing keys over insecure communication channels or storing them in plaintext.
- Key revocation: Establish mechanisms to revoke compromised or compromised keys promptly. Revoked keys should no longer be used for encryption or decryption.
- Backup and recovery: Implement regular backups of encryption keys to ensure their availability in case of data loss or system failures. Test the key recovery process to verify its effectiveness.
By implementing robust key management practices, organizations can safeguard the encryption keys and maintain the integrity and confidentiality of the encrypted data.
Secure Data Transmission

Secure data transmission ensures that data remains confidential and protected during transit between systems or over networks. It prevents unauthorized interception or tampering of sensitive information. Here are some key points to consider for secure data transmission:
- Transport Layer Security (TLS): Use TLS protocols to establish secure encrypted connections between systems. TLS ensures the confidentiality and integrity of data transmitted over insecure networks.
- Certificate management: Obtain and manage digital certificates from trusted certificate authorities to enable secure communicationbetween systems. Certificates validate the authenticity of the communicating parties and enable secure encryption key exchange.
- Secure protocols: Utilize secure communication protocols, such as HTTPS for web traffic or SFTP for file transfers, that provide encryption and authentication mechanisms.
- Secure configuration: Configure systems and applications to use secure communication protocols and enforce strong encryption algorithms. Disable insecure or outdated protocols, such as SSL.
- Data integrity checks: Implement mechanisms, such as message authentication codes (MAC) or digital signatures, to verify the integrity of transmitted data and detect any tampering attempts.
- Secure endpoints: Ensure that both the sending and receiving systems have appropriate security measures in place, including up-to-date software, firewalls, and intrusion detection systems, to protect against attacks.
By implementing secure data transmission mechanisms, organizations can mitigate the risk of data interception or tampering during transit.
Secure Database Design
Secure database design focuses on protecting data stored in databases from unauthorized access or data breaches. It involves implementing robust security controls and access restrictions. Here are some key points to consider for secure database design:
- Database access controls: Implement strong authentication and authorization mechanisms to control access to the database. Use role-based access controls (RBAC) to restrict privileges based on user roles.
- Least privilege principle: Grant users the minimum privileges necessary to perform their tasks. Avoid granting unnecessary administrative or superuser privileges that can increase the risk of unauthorized access.
- Database encryption: Encrypt sensitive data stored in the database to protect it from unauthorized access in case of a breach. Use transparent data encryption (TDE) or column-level encryption for sensitive fields.
- Secure database connections: Ensure that database connections are established securely using encrypted protocols, such as SSL/TLS. Encrypt data transmitted between the application and the database.
- Database activity monitoring: Implement database activity monitoring and auditing mechanisms to detect and respond to suspicious activities or potential security breaches.
- Regular patching and updates: Keep the database software and associated components up to date with the latest security patches and updates to address any known vulnerabilities.
By implementing secure database design principles, organizations can protect the integrity and confidentiality of their stored data.
Secure File Storage

Secure file storage focuses on protecting sensitive files and documents from unauthorized access or data leakage. It involves implementing appropriate access controls, encryption, and secure storage mechanisms. Here are some key points to consider for secure file storage:
- Access controls: Apply access controls to files and directories to restrict access to authorized individuals or groups. Use file permissions and access control lists (ACLs) to manage file-level security.
- File encryption: Encrypt sensitive files stored in storage systems or file servers to protect them from unauthorized access or data theft. Use strong encryption algorithms and secure key management practices.
- Secure file transfer: When transferring files between systems or users, utilize secure file transfer protocols that provide encryption and authentication, such as SFTP or SCP.
- Secure storage systems: Implement secure storage systems that provide built-in encryption and access controls. Examples include encrypted network-attached storage (NAS) or cloud storage solutions with robust security features.
- Data backup and disaster recovery: Regularly back up sensitive files and implement disaster recovery plans to ensure data availability and protect against data loss or system failures.
- File integrity checks: Implement mechanisms to verify the integrity of stored files, such as file hashing or digital signatures, to detect any unauthorized modifications or tampering.
By implementing secure file storage practices, organizations can protect sensitive files from unauthorized access, data leakage, or manipulation.
Conclusion
In conclusion, secure data storage and encryption techniques are crucial for protecting sensitive information in applications. By implementing data classification, selecting appropriate encryption algorithms, ensuring robust key management, securing data transmission, designing secure databases, and implementing secure file storage mechanisms, organizations can mitigate the risk of unauthorized access or data breaches. It is important to regularly assess and update security measures to address emerging threats and vulnerabilities. By following best practices and staying informed about the latest security advancements, organizations can effectively safeguard their data and maintain the trust of their users.

