Designing a secure network architecture is crucial for protecting applications from network-based attacks and ensuring the confidentiality, integrity, and availability of sensitive data. A robust network architecture incorporates various security measures, such as network segmentation, firewall configurations, intrusion detection and prevention systems, secure remote access, and network traffic encryption. This article will explore the principles and considerations for designing a secure network architecture for applications, providing practical examples and actionable tips for implementing these best practices effectively.
Network Segmentation
Network segmentation involves dividing a network into smaller, isolated segments to control and restrict the flow of network traffic. By implementing network segmentation, organizations can minimize the impact of potential security breaches and limit lateral movement within the network. Here are some key points to consider for network segmentation:
- Identify critical assets and data: Determine the critical assets and data that require the highest level of protection. This could include sensitive databases, intellectual property, or customer information.
- Logical and physical segmentation: Implement both logical and physical segmentation. Logical segmentation involves using virtual LANs (VLANs), access control lists (ACLs), or software-defined networking (SDN) to separate network traffic. Physical segmentation involves using separate physical network devices or dedicated network appliances to isolate traffic.
- Demilitarized Zone (DMZ): Create a DMZ to provide a secure zone for hosting public-facing applications or services. Place the DMZ between the external and internal networks, isolating the publicly accessible systems from the internal network.
- Segmentation based on trust levels: Group resources and systems with similar trust levels together. For example, separate internal employee networks from guest networks or contractor networks. This helps prevent unauthorized access or lateral movement between different trust zones.
- Access controls: Apply access controls, such as firewalls and access control lists (ACLs), to regulate the traffic flow between network segments. Only allow necessary communication between segments and restrict access to sensitive resources based on user roles and permissions.
- Monitoring and logging: Implement network monitoring and logging mechanisms to detect and respond to any suspicious activities or unauthorized attempts to access segmented networks.
By implementing network segmentation, organizations can enhance the security of their network architecture and limit the impact of potential security breaches.
Firewall Configurations
Firewalls play a critical role in network security by controlling and filtering network traffic based on predefined security policies. Proper firewall configurations help protect applications from unauthorized access, network-based attacks, and the spread of malware. Here are some key points to consider for firewall configurations:
- Default deny policy: Configure firewalls with a default deny policy, allowing only explicitly permitted traffic. By denying all traffic by default and allowing only the necessary traffic, organizations can minimize the attack surface.
- Application-aware firewalls: Use application-aware firewalls that can identify and understand the specific protocols and traffic patterns associated with different applications. This allows for more granular control and enables the firewall to detect and block application-layer attacks.
- Segment-specific firewalls: Implement firewalls at the boundaries of network segments to control traffic flow between different segments. This adds an extra layer of security and ensures that traffic between segments is only allowed based on predefined rules.
- Intrusion Prevention System (IPS): Combine firewall capabilities with intrusion prevention systems to proactively detect and prevent network-based attacks. IPS can inspect network traffic for known attack patterns and take action to block or mitigate the attacks.
- Regular rule review and updates: Regularly review firewall rules to ensure they are still relevant and aligned with the organization’s security policies. Remove any unnecessary or outdated rules. Update firewall rules promptly to address emerging threats or changes in business requirements.
- Logging and monitoring: Enable firewall logging and implement a centralized log management system to collect and analyze firewall logs. Regularly monitor firewall logs for any suspicious activities or attempts to circumvent the firewall rules.
By following these best practices for firewall configurations, organizations can strengthen their network security and protect applications from unauthorized access and network-based attacks.
Intrusion Detection and Prevention Systems (IDPS)
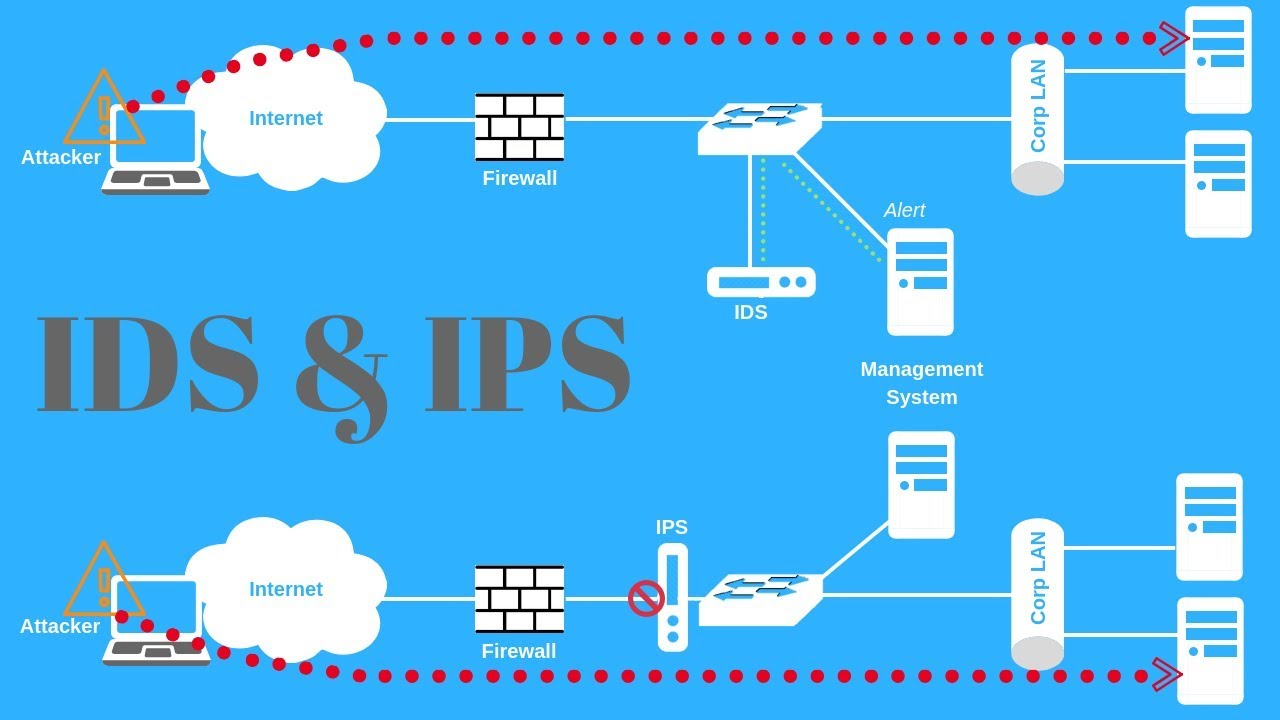
Intrusion detection and prevention systems (IDPS) play a crucial role in network security by monitoring network traffic for signs of unauthorized or malicious activities and taking appropriate action to mitigate or prevent attacks. Here are some key points to consider for IDPS:
- Network-based and host-based IDPS: Implement both network-based and host-based IDPS solutions. Network-based IDPS monitors network traffic and detects anomalies or known attack patterns, while host-based IDPS focuses on individual systems or hosts and detects suspicious activities or unauthorized access attempts.
- Signature-based and behavior-based detection: Utilize both signature-based and behavior-based detection techniques. Signature-based detection relies on known patterns of attacks, while behavior-based detection analyzes the behavior of network traffic or system activities to identify anomalous or malicious behavior.
- Real-time alerts and notifications: Configure IDPS to generate real-time alerts and notifications when suspicious activities oranomalous behavior is detected. These alerts should be sent to security administrators or a security operations center (SOC) for immediate investigation and response.
- Integration with other security systems: Integrate IDPS with other security systems, such as firewalls, SIEM (Security Information and Event Management) solutions, and threat intelligence platforms. This enables better correlation and analysis of security events and enhances the effectiveness of the overall security infrastructure.
- Regular updates and patches: Keep IDPS systems up to date with the latest signatures, patches, and software updates. New attack techniques and vulnerabilities are constantly emerging, and regular updates ensure that the IDPS can effectively detect and prevent the latest threats.
- Tuning and customization: Fine-tune and customize IDPS configurations to align with the organization’s specific needs and security requirements. Adjust detection thresholds, create custom signatures, and define specific rules or policies based on the organization’s unique network environment and threat landscape.
By implementing IDPS solutions and following these best practices, organizations can enhance their ability to detect and respond to network-based attacks, protecting their applications and sensitive data.
Secure Remote Access
Secure remote access is essential for organizations that allow their employees, partners, or contractors to access network resources from remote locations. However, remote access introduces additional security risks, and it is crucial to implement robust measures to ensure the confidentiality and integrity of data transmitted over remote connections. Here are some key points to consider for secure remote access:
- Virtual Private Network (VPN): Use VPN technologies to establish secure encrypted tunnels between remote devices and the corporate network. VPNs provide confidentiality and integrity by encrypting data and authenticating remote users or devices before granting access.
- Multi-factor authentication (MFA): Implement multi-factor authentication for remote access. MFA combines multiple authentication factors, such as passwords, smart cards, biometrics, or one-time passwords, to provide an extra layer of security beyond just username and password authentication.
- Access controls and user permissions: Enforce access controls and user permissions to ensure that remote users have appropriate access privileges based on their roles and responsibilities. Limit access to only the resources and systems necessary for remote work.
- Session monitoring and logging: Implement session monitoring and logging for remote access sessions. This allows organizations to track and audit remote activities, detect any suspicious behavior, and investigate potential security incidents.
- Endpoint security: Ensure that remote devices meet the organization’s security requirements, such as having up-to-date antivirus software, firewalls, and operating system patches. Implement endpoint security solutions to protect remote devices from malware and other threats.
- Secure remote administration: Implement secure protocols, such as Secure Shell (SSH), for remote administration of network devices or servers. Disable unnecessary remote administration protocols and services to minimize the attack surface.
By implementing these best practices for secure remote access, organizations can enable remote work while minimizing the risk of unauthorized access or data breaches.
Network Traffic Encryption

Network traffic encryption is essential for protecting the confidentiality and integrity of data transmitted over the network. Encrypting network traffic prevents eavesdropping and unauthorized interception of sensitive information. Here are some key points to consider for network traffic encryption:
- Transport Layer Security (TLS) and Secure Sockets Layer (SSL): Use TLS and SSL protocols to encrypt network traffic between clients and servers. These protocols provide secure communication channels and ensure that data transmitted over the network is encrypted and protected from interception.
- Encrypting internal network traffic: Consider encrypting internal network traffic, especially in environments where sensitive data or critical systems are present. This helps protect against insider threats and unauthorized access to internal network segments.
- Certificate management: Implement proper certificate management practices, including the use of trusted certificates issued by reputable certificate authorities (CAs). Regularly update and renew certificates to ensure their validity and prevent potential security vulnerabilities.
- Encryption for remote connections: Ensure that remote connections, such as VPN connections or remote desktop sessions, are encrypted using strong encryption algorithms. Avoid using outdated or weak encryption algorithms that can be easily compromised.
- Application-level encryption: Consider implementing application-level encryption for sensitive data, especially when transmitting data over untrusted networks or storing data in databases. Application-level encryption provides an extra layer of protection, even if network-level encryption is compromised.
- Periodic encryption audits: Conduct periodic encryption audits to ensure that encryption is properly implemented and configured. Test the effectiveness of encryption mechanisms and verify that encryption is consistently applied across the network infrastructure.
By prioritizing network traffic encryption and following these best practices, organizations can safeguard the confidentiality and integrity of their data as it traverses the network.

