Implementing robust user access controls is essential for ensuring proper authentication and authorization mechanisms in applications. User access controls help prevent unauthorized access to sensitive information and protect user data. This article will provide guidance on best practices for implementing effective user access controls. It will cover topics such as strong password policies, multi-factor authentication (MFA), session management, role-based access control (RBAC), and the least privilege principle.
Strong Password Policies

Enforcing strong password policies is a fundamental aspect of user access controls. Weak passwords can be easily compromised, making it easier for attackers to gain unauthorized access to user accounts. Here are some key points to consider for implementing strong password policies:
- Password complexity: Require users to create passwords that meet specific complexity requirements, such as a minimum length, a mix of uppercase and lowercase letters, numbers, and special characters.
- Password expiration: Set password expiration policies to ensure that users regularly update their passwords. It helps mitigate the risk of compromised passwords being used for prolonged periods.
- Password history: Prevent users from reusing their previous passwords. Maintain a password history to track and enforce password uniqueness.
- Account lockouts: Implement mechanisms to lock user accounts after a certain number of failed login attempts. This helps protect against brute-force attacks.
- Password storage: Store passwords securely using strong hashing algorithms and salt values to prevent the exposure of plaintext passwords in case of a data breach.
By implementing strong password policies, organizations can significantly reduce the risk of unauthorized access due to weak or compromised passwords.
Multi-Factor Authentication (MFA)
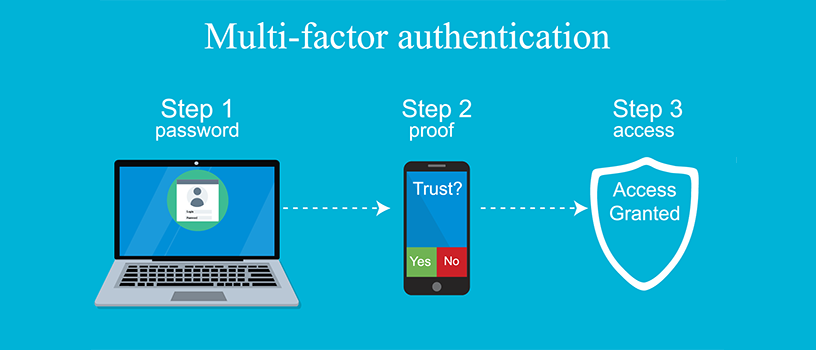
Multi-factor authentication provides an additional layer of security by requiring users to provide multiple forms of authentication to access their accounts. It adds an extra barrier for attackers, even if they manage to obtain the user’s password. Here are some key points to consider for implementing multi-factor authentication:
- Two-factor authentication (2FA): Implement 2FA, which typically involves combining something the user knows (password) with something the user possesses (e.g., a unique code sent to their mobile device) for authentication.
- Biometric authentication: Utilize biometric authentication methods, such as fingerprint or facial recognition, as an additional factor in the authentication process.
- Time-based One-Time Password (TOTP): Use TOTP algorithms, such as Google Authenticator or Authy, to generate one-time passwords that expire after a short period. This can be used as an additional factor for authentication.
- Hardware tokens: Provide users with hardware tokens, such as smart cards or USB tokens, that generate unique codes for authentication.
- Push notifications: Implement push notification-based authentication, where users receive a notification on their trusted devices and confirm the login attempt.
By implementing multi-factor authentication, organizations can significantly enhance the security of user accounts and protect against unauthorized access, even if passwords are compromised.
Session Management
Effective session management ensures that user sessions remain secure throughout their interaction with an application. It involves managing session identifiers, session timeouts, and implementing measures to prevent session hijacking or fixation attacks. Here are some key points to consider for session management:
- Secure session identifiers: Generate secure and random session identifiers that are resistant to guessing or brute-force attacks. Use a combination of letters, numbers, and special characters.
- Session timeouts: Set appropriate session timeouts to automatically log out inactive users. Shorter timeouts provide better security but should balance usability considerations.
- Session encryption: Encrypt session data, such as session identifiers or user information, to protect it from unauthorized access or tampering.
- Secure cookie attributes: Utilize secure cookie attributes, such as the Secure flag and HttpOnly flag, to ensure that cookies are only transmitted over secure connections and cannot be accessed by client-side scripts.
- Session monitoring and auditing: Implement mechanisms to monitor and audit session activities, including login attempts, session creations, and session terminations. This helps detect and respond to suspicious session activities.
- Protection against session attacks: Implement measures to prevent session attacks, such as session hijacking or fixation. Use techniques like session token regeneration upon authentication or implementing anti-CSRF (Cross-Site Request Forgery) tokens.
By effectively managing user sessions, organizations can mitigate the risk of unauthorized access or session-related attacks.
Role-Based Access Control (RBAC)
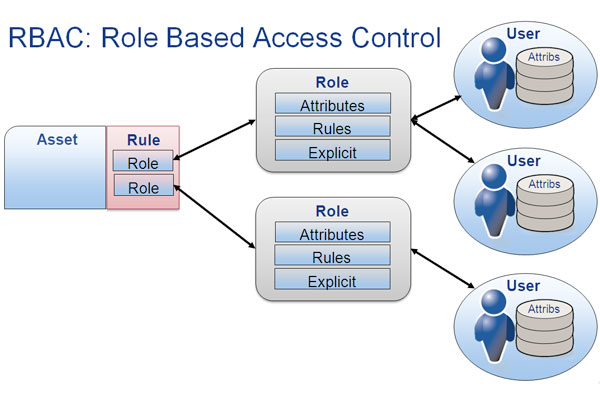
Role-Based Access Control (RBAC) is a widely adopted approach for managing user access rights based on their roles and responsibilities within an organization. RBAC ensures that users have the necessary privileges to perform their tasks while preventing unauthorized access to sensitive information. Here are some key points to consider for implementing RBAC:
- Role definition: Define roles based on job functions or responsibilities within the organization. Roles should be granular and reflect the specific access needs of each user.
- Privilege assignment: Assign appropriate permissions to each role based on the tasks and dataaccess requirements. Grant the minimum privileges necessary for users to perform their job functions effectively.
- User-role assignment: Associate users with specific roles based on their job roles or responsibilities. Ensure that user-role assignments are regularly reviewed and updated as employees change roles or leave the organization.
- Role hierarchy: Establish a role hierarchy if needed, where higher-level roles inherit permissions from lower-level roles. This simplifies role management and ensures consistency.
- Regular access reviews: Conduct regular access reviews to validate that user-role assignments are accurate and up-to-date. Remove unnecessary or excessive privileges from users who no longer require them.
- Separation of duties: Implement separation of duties by assigning conflicting roles or permissions to different users. This ensures that no single user has excessive control or access to critical systems or data.
By implementing RBAC, organizations can streamline user access management, reduce the risk of unauthorized access, and enforce the principle of least privilege.
Least Privilege Principle

The principle of least privilege (PoLP) dictates that users should be granted the minimum privileges necessary to perform their job functions effectively. By limiting user access to only what is required, organizations can minimize the impact of potential security breaches and prevent unauthorized actions. Here are some key points to consider for implementing the least privilege principle:
- Inventory of privileges: Conduct an inventory of all privileges and permissions within the organization’s systems and applications. Identify and document the specific access rights associated with each privilege.
- User access review: Regularly review user access rights to ensure that users have only the privileges necessary for their job roles. Remove unnecessary or excessive privileges promptly.
- Just-in-time privileges: Implement just-in-time (JIT) privileges, where users are granted temporary elevated privileges for specific tasks or timeframes. This reduces the exposure of privileged access and minimizes the risk of abuse.
- Privilege escalation controls: Implement controls to prevent unauthorized privilege escalation. Monitor and log privilege escalations to detect and respond to potential security breaches.
- Monitoring and auditing: Implement robust monitoring and auditing mechanisms to track user activities, especially those with elevated privileges. This helps detect and investigate any unauthorized actions or suspicious behaviors.
- User education and awareness: Educate users about the importance of the least privilege principle and the potential risks associated with excessive privileges. Encourage responsible access management practices.
By adhering to the least privilege principle, organizations can significantly reduce the attack surface and limit the potential damage caused by compromised accounts or insider threats.
Conclusion
In conclusion, implementing effective user access controls is crucial for ensuring proper authentication and authorization mechanisms in applications. By following best practices such as enforcing strong password policies, implementing multi-factor authentication, managing user sessions securely, adopting role-based access control, and adhering to the least privilege principle, organizations can significantly enhance their security posture and protect their sensitive information from unauthorized access. Remember to regularly review and update access controls based on changing business needs and evolving security threats. By incorporating these best practices into their applications, organizations can build a strong foundation for protecting user data and maintaining the trust of their users.

