Securing application programming interfaces (APIs) is crucial in mobile app development to protect sensitive data and prevent unauthorized access to backend systems. APIs serve as the bridge between mobile apps and servers, allowing them to exchange data and perform various functionalities. In this article, we will discuss essential tips for developers to secure mobile app APIs effectively. We will explore authentication mechanisms, authorization controls, input validation, and other security measures that developers should implement to safeguard their APIs from unauthorized access and misuse.
Authentication Mechanisms for Mobile App APIs
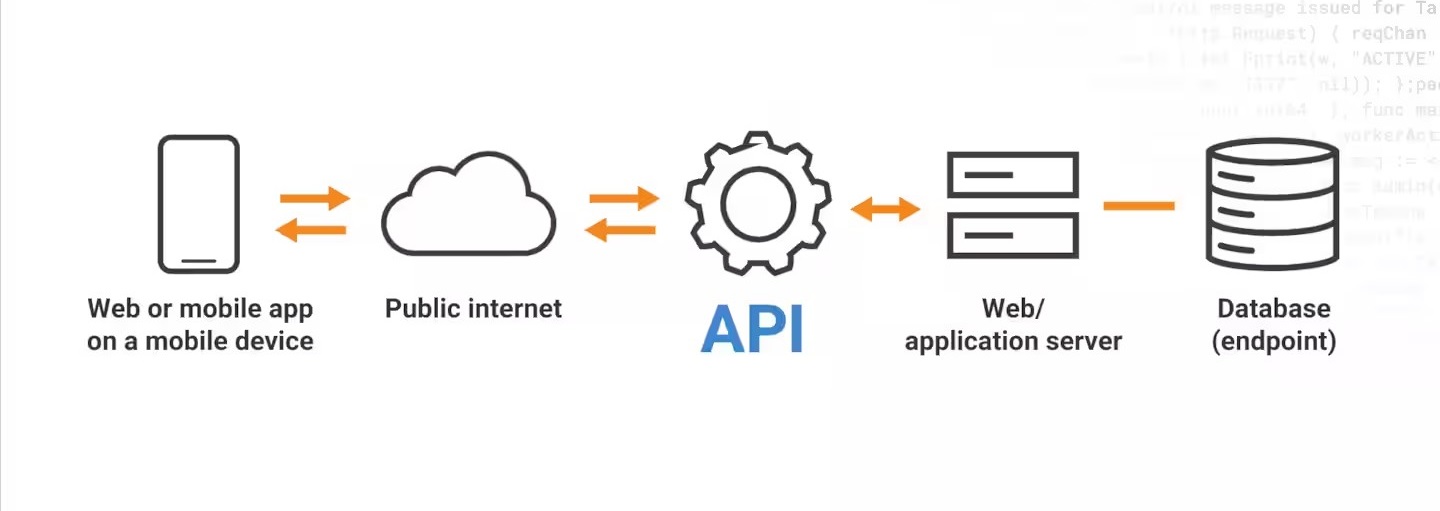
Authentication is the process of verifying the identity of users or applications accessing an API. Implementing robust authentication mechanisms is vital to prevent unauthorized access to sensitive data and ensure that only legitimate requests are processed. Here are some key tips for implementing authentication in mobile app APIs:
- Token-based Authentication: Instead of relying on traditional username-password authentication, consider implementing token-based authentication mechanisms such as JSON Web Tokens (JWT) or OAuth. Tokens are issued upon successful authentication and are sent with subsequent API requests to validate the authenticity of the request. Tokens can have expiration times, reducing the risk of long-term compromised credentials.
- Secure Storage of Credentials: If your API requires traditional username-password authentication, ensure that user credentials are securely stored on the server. Apply strong hashing algorithms such as bcrypt or Argon2 to hash and salt passwords, making them resistant to brute-force attacks. Avoid storing plaintext passwords and enforce secure password policies to enhance authentication security.
- Multi-factor Authentication (MFA): Consider implementing MFA as an additional layer of security for sensitive mobile app APIs. MFA requires users to provide multiple forms of authentication, such as a password and a one-time verification code sent to their registered email or mobile device. MFA can significantly reduce the risk of unauthorized access, even if credentials are compromised.
- Rate Limiting and Account Lockouts: Implement rate limiting mechanisms to prevent brute-force attacks and account enumeration. Limit the number of API requests that can be made within a certain time frame for each user or IP address. Additionally, consider implementing account lockouts or temporary suspensions after multiple failed authentication attempts to mitigate the risk of credential guessing attacks.
Authorization Controls for Mobile App APIs
Authorization controls ensure that authenticated users or applications have the appropriate permissions to access specific API resources. By implementing proper authorization mechanisms, developers can prevent unauthorized access to sensitive data and enforce access restrictions based on user roles and privileges. Consider the following tips for implementing authorization controls in mobile app APIs:
- Role-Based Access Control (RBAC): Adopt RBAC to manage access rights based on user roles. Assign different roles to users or applications and define the permissions associated with each role. For example, an API may have roles such as “admin,” “user,” and “guest,” each with different levels of access to resources. Ensure that API endpoints enforce proper authorization checks based on the roles associated with the authenticated user.
- Fine-Grained Access Control: In addition to RBAC, consider implementing fine-grained access controls to provide more granular permissions. Fine-grained access control allows you to define specific access privileges for individual API resources or data elements within a resource. It provides a higher level of control over what actions and data each user or role can access.
- API Key Management: If your mobile app API is meant to be accessed by third-party developers or other applications, consider implementing API key-based authentication and authorization. Each authorized application is assigned a unique API key that it includes in API requests. API keys help track and control API usage, and they can be revoked if misuse or abuse is detected.
- Regular Access Rights Review: Periodically review and update access rights and permissions associated with user roles. Conduct regular audits to ensure that access controls remain aligned with the evolving requirements of your mobile app and backend systems. Remove unnecessary privileges and promptly revoke access for users who no longer require API access.
Input Validation and Data Sanitization for Mobile App APIs
Input validation and data sanitization are essential security measures to protect mobile app APIs from common web vulnerabilities, such as injection attacks and cross-site scripting (XSS). By validating and sanitizing user input, developers can prevent malicious data from compromising the integrity and security of their APIs. Consider the following tips for implementing input validation and data sanitization in mobile app APIs:
- Input Validation: Validate all input received from mobile app clients before processing it. Implement server-side input validation to ensure that only expected and valid data is accepted. Validate data types, lengths, and formats to prevent injection attacks and other security vulnerabilities. Use secure programming practices and frameworks that provide built-in input validation mechanisms.
- Parameterized Queries: When interacting with databases or executing SQL queries, utilize parameterized queries or prepared statements. Parameterized queries separate the SQL logic from the user input, preventing SQL injection attacks. Ensure that all user-supplied data is properly escaped and parameterized to avoid the risk of maliciousSQL code execution.
- Output Encoding: Sanitize and encode all output data before sending it back to mobile app clients. Apply appropriate encoding techniques such as HTML entity encoding or URL encoding to prevent cross-site scripting (XSS) attacks. By encoding output data, you ensure that any potentially malicious code is treated as literal data and not executed by the client’s browser.
- Content Security Policy (CSP): Implement a Content Security Policy to control the types of content that can be loaded by your mobile app API. CSP allows you to define trusted sources for scripts, stylesheets, images, and other resources, reducing the risk of code injection and malicious content execution. By specifying strict content security policies, you can mitigate the impact of any potential vulnerabilities in the mobile app or its dependencies.
Other Security Measures for Mobile App APIs
Apart from authentication, authorization, and input validation, there are other security measures that developers should consider when securing mobile app APIs. These additional measures can further enhance the overall security posture and protect against emerging threats. Here are some important tips:
- Transport Layer Security (TLS): Implement TLS encryption to secure the communication between the mobile app clients and the API server. Use industry-standard protocols and strong cipher suites to ensure data confidentiality and integrity during transit. Enable certificate pinning to prevent man-in-the-middle attacks and validate the authenticity of the server’s SSL/TLS certificate.
- API Security Testing: Regularly perform security testing on your mobile app APIs to identify vulnerabilities and weaknesses. Conduct penetration testing, vulnerability scanning, and code reviews to uncover any potential security flaws. Consider using automated tools and manual testing techniques to assess the security of your APIs comprehensively.
- API Logging and Monitoring: Implement robust logging and monitoring mechanisms for your mobile app APIs. Log API requests and responses, including relevant metadata such as client IP addresses and user agents. Monitor API activity for suspicious patterns or unexpected behavior. Establish alerts and notifications to promptly identify and respond to potential security incidents.
- Secure API Documentation: Ensure that your API documentation does not reveal sensitive information or provide excessive details about your backend systems. Limit the visibility of sensitive API endpoints and their functionalities to authorized users. Avoid including sensitive data, such as API keys or database credentials, in publicly accessible documentation.
Conclusion
Securing mobile app APIs is of utmost importance to protect sensitive data, prevent unauthorized access, and maintain the trust of users. By implementing strong authentication mechanisms, robust authorization controls, input validation, and other security measures, developers can significantly enhance the security posture of their APIs. Remember to regularly update and review security measures as new threats emerge. By prioritizing API security throughout the development lifecycle, developers can ensure that their mobile app APIs remain resilient against evolving security challenges.

