In today’s technology-driven world, it is crucial to prioritize security throughout the software development lifecycle (SDLC). By integrating security measures from the initial stages of development, organizations can significantly reduce the risk of vulnerabilities and mitigate potential threats. This article will provide a comprehensive guide on implementing a secure SDLC, covering essential aspects such as threat modeling, secure coding practices, security testing, code reviews, and security-focused documentation.
Threat Modeling
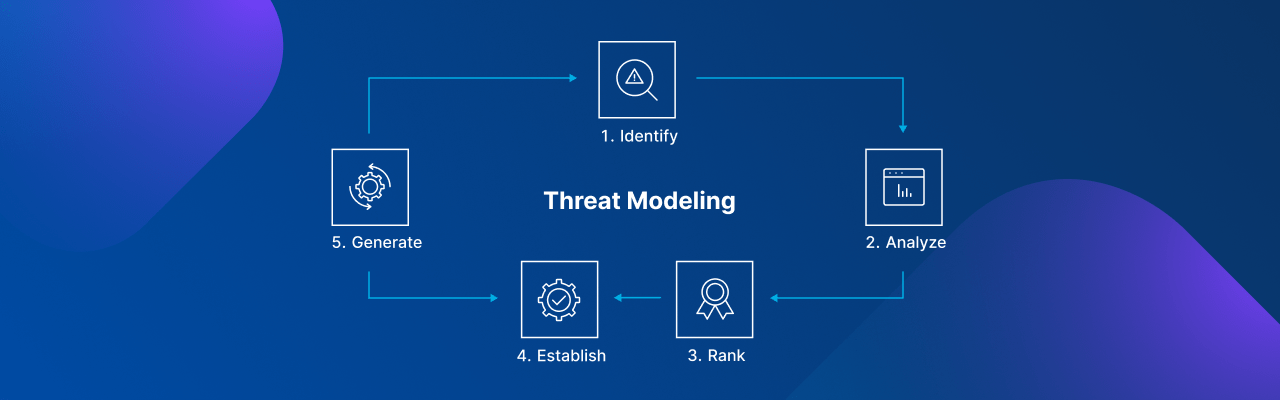
Threat modeling is an essential step in building secure software. It involves identifying potential threats and vulnerabilities and assessing their potential impact on the system. By conducting threat modeling early in the SDLC, developers can proactively address security risks and design robust countermeasures. Here are some key points to consider in threat modeling:
- Identify and prioritize assets: Begin by identifying the critical assets and resources within the software system. These can include user data, sensitive information, intellectual property, or any other valuable assets.
- Identify potential threats: Identify potential threats that could exploit vulnerabilities in the system. This can include external threats like hackers, malware, or internal threats such as unauthorized access by employees.
- Assess potential vulnerabilities: Evaluate the system’s design, architecture, and implementation to identify potential vulnerabilities. This can be done through architecture reviews, code analysis, and security testing.
- Determine impact: Assess the potential impact of each identified threat on the system. This helps prioritize mitigation efforts and allocate resources effectively.
- Design countermeasures: Develop appropriate countermeasures and security controls to mitigate the identified threats. This can include implementing access controls, encryption, input validation, and secure authentication mechanisms.
By following these steps, organizations can systematically identify and address security threats early in the development process, reducing the likelihood of security breaches.
Secure Coding Practices

Secure coding practices play a crucial role in preventing common software vulnerabilities. By adopting secure coding techniques, developers can minimize the risk of introducing security flaws into the software. Here are some essential considerations for secure coding practices:
- Input validation: Validate and sanitize all user inputs to prevent common vulnerabilities like injection attacks (e.g., SQL injection, command injection). Use appropriate validation techniques depending on the input type (e.g., regular expressions, parameterized queries).
- Avoid hardcoded credentials: Avoid hardcoding sensitive information such as passwords, API keys, or encryption keys within the source code. Instead, securely store them in configuration files or leverage secure key management systems.
- Secure authentication and authorization: Implement secure authentication mechanisms, such as multi-factor authentication (MFA) and strong password policies. Use proper authorization techniques to ensure users have appropriate access rights and permissions.
- Secure error handling: Implement proper error handling mechanisms to avoid revealing sensitive information to potential attackers. Error messages should be informative to developers but not disclose any sensitive details to the end-users.
- Secure session management: Implement secure session management practices, including session expiration, secure cookie handling, and protection against session hijacking or fixation attacks.
- Secure communication: Use secure communication protocols (e.g., HTTPS) to protect sensitive data during transit. Implement secure encryption algorithms and avoid using weak or deprecated cryptographic functions.
- Regularly update dependencies: Keep all software dependencies up to date to mitigate the risk of known vulnerabilities. Regularly monitor security advisories and apply patches promptly.
By following these secure coding practices, developers can significantly reduce the risk of introducing security vulnerabilities into the software.
Security Testing

Thorough security testing is vital to identify and remediate vulnerabilities in software applications. It helps ensure that the implemented security controls and countermeasures are effective and robust. Here are some key points to consider for security testing:
- Penetration testing: Conduct penetration testing to simulate real-world attacks and identify vulnerabilities that could be exploited by attackers. This involves systematically assessing the application’s security posture and attempting to exploit vulnerabilities.
- Vulnerability scanning: Use automated vulnerability scanning tools to identify common vulnerabilities such as outdated libraries, misconfigurations, or known security issues.
- Code analysis: Utilize static code analysis tools to identify potential security vulnerabilities in the source code. These tools can detect common coding mistakes, insecure coding patterns, and potential security risks.
- Fuzz testing: Perform fuzz testing to identify vulnerabilities related to input validation and boundary checking. Fuzzing involves supplying the application with invalid, unexpected, or random inputs to uncover potential weaknesses.
- Security regression testing: Incorporate security-specific test cases into the regular regression testing process. This ensures that security controls remain effective even after changes or updates to the software.
- Secure configuration testing: Verify that the software is securely configured by testing various configuration settings. This includes checking for default or weak passwords, unnecessary services or features, and proper access controls.
By conducting thorough security testing, organizations can identify and address vulnerabilities before the software is deployed, reducing the likelihood of successful attacksand improving overall software security.
Code Reviews

Code reviews are an essential part of the software development process. They provide an opportunity for developers to share knowledge, identify potential issues, and ensure that secure coding practices are followed. Here are some key points to consider for conducting effective security-focused code reviews:
- Establish code review guidelines: Define clear guidelines that highlight security considerations during code reviews. These guidelines should cover secure coding practices, common vulnerabilities to look for, and best practices for addressing them.
- Involve security experts: Engage security experts or dedicated security personnel during code reviews to provide specialized insights and identify potential security flaws.
- Review security controls: Ensure that the implemented security controls, such as input validation, authentication mechanisms, and access controls, are correctly implemented and effective in mitigating potential threats.
- Identify security vulnerabilities: Look for common security vulnerabilities, including injection attacks, cross-site scripting (XSS), cross-site request forgery (CSRF), and insecure direct object references (IDOR). Scrutinize the code for potential weaknesses that could be exploited by attackers.
- Review third-party libraries: Assess the security of third-party libraries or components used in the software. Check for known vulnerabilities, outdated versions, or insecure configurations. Consider using trusted sources and performing due diligence before incorporating third-party code.
- Provide actionable feedback: During code reviews, provide actionable feedback to developers on identified security issues. Clearly explain the risks associated with each issue and suggest appropriate remediation techniques.
By incorporating security-focused code reviews into the development process, organizations can identify and rectify security vulnerabilities early on, ensuring the production of more secure software.
Security-Focused Documentation

Comprehensive and well-documented security practices and guidelines are essential for maintaining a secure SDLC. They provide developers with the necessary information and instructions to implement security measures effectively. Here are some key points to consider when creating security-focused documentation:
- Security requirements: Clearly define security requirements for the software. Specify the minimum security standards, compliance requirements, and any industry-specific security guidelines that need to be followed.
- Secure coding guidelines: Document secure coding practices and guidelines that developers should adhere to. Include examples and explanations of common vulnerabilities and how to mitigate them.
- Security architecture: Document the security architecture of the software, including the design principles, security controls, and layers of defense. Explain how different components interact and ensure the security of the overall system.
- Threat modeling documentation: Document the threat modeling process, including the identified threats, vulnerabilities, and countermeasures. This documentation helps maintain a record of the security considerations and decisions made during the development process.
- Security testing procedures: Document the procedures and methodologies for security testing, including penetration testing, vulnerability scanning, and code analysis. Provide guidelines for interpreting and addressing the findings from security testing activities.
- Security incident response: Outline the procedures and guidelines for responding to security incidents or breaches. Document the steps to be followed, responsible personnel, and communication protocols in the event of a security incident.
By providing comprehensive security-focused documentation, organizations ensure that developers have the necessary information and resources to implement security measures effectively throughout the SDLC.
Conclusion
In conclusion, integrating security into the software development lifecycle is crucial for building secure software applications. By following the practices outlined in this article, including threat modeling, secure coding practices, security testing, code reviews, and security-focused documentation, organizations can significantly enhance the security posture of their software. Remember that security is an ongoing process, and it is essential to continuously monitor, update, and adapt security measures as new threats and vulnerabilities emerge. By prioritizing security throughout the SDLC, organizations can protect sensitive data, prevent security breaches, and build trust with their users and customers.

